Enterprise WIFI Hacking with Hostapd-WPE
Recently we have been on Wireless Pentest with end goal to compromise the credentials of the end user and try to escalate rights to compromise Domain Admins account. The customer in my case was running WPA2 Enterprise with PEAP enabled.
Earlier we use to need the specific version of Kali along with freeradius server with WPE (Wireless Pwnage Edition) patch and hostapd. Now couple of months back Kali rolling got the hostapd-wpe as base package. In this you don't need the freeradius server to be downloaded separately. Old method of attack is mentioned here.
Lets start looking at current setup, from hardware perspective we are using TP-LINK TL-WN722N (version 1.1, not version 2.0) or Alfa AWUS036NHA wireless card and Kali rolling 2016.2. Both these card have Atheros AR9271 chipset and supports attacking 2.4 Ghz spectrum.
In case you have 5 Ghz as target network, you can use Alfa AWUS036ACH for which Kali added support in 2017.1 rolling release. ( This card supports both 2.4 and 5 Ghz)
In case you have 5 Ghz as target network, you can use Alfa AWUS036ACH for which Kali added support in 2017.1 rolling release. ( This card supports both 2.4 and 5 Ghz)
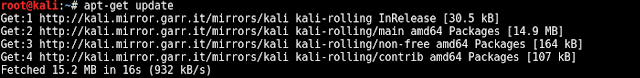
First step here is to update the Kali version, by running below command, once updated install the hostapd-wpe
Connect the TP-link wireless card to machine with Kali running. Also check whether interface is detected by Kali using iwconfig command. Then run airmon-ng along with “check kill”, this will check and kill off processes that might interfere with the aircrack-ng suite.
After this, configure AP properties by editing /etc/hostapd-wpe/hostapd-wpe.conf like updating the AP name which would lure the victims. Then using the hostapd-wpe and respective config file we start the AP which would capture hashes of the users authenticating to our spoofed AP.
Once the victims connects to attacker advertised AP, the challenge and response of the users would be printed on the screen of hostapd-wpe.
But using above setup is enough to capture hashes of victims who are less wifi security aware, because when victim connects to our advertised AP, he is asked to Trust the fake certificate i.e.; "Example Server Certificate" which might raise some concerns.
Editing default certificate details might be pain in order to match the genuine certificate, so to aid us there is python script by name apd_launchpad which convenient way to create a hostapd-wpe configuration file and the associated spoofed certificates.
So, download the python script in hostapd-wpe certs directory.
We can use below mentioned minimum flags to generate the certificate matching our customer (DEMOBANK) certificate and also the configuration file too.
The configuration file and certs are saved in DEMOBANK folder.
Lets run the generated config (DEMOBANK.conf) along using hostapd-wpe.
Now the victims would see the certificate matching to genuine one (less suspicion)
After running this for sometime, we were able to grab hashes of the victims.
Once a challenge and response are obtained, crack them using asleap or hashcat, together with a password dictionary file.
root@kali:~# zcat rockyou.txt.gz | asleap -C <Challenge> -R <Response> -W -
or
root@kali:~# ./hashcat64.bin -D1 -a 0 -m 5500 hash.txt dictionary.txt -r rule.txt
root@kali:~# ./hashcat64.bin -D1 -a 0 -m 5500 hash.txt dictionary.txt -r rule.txt
Cracked credentials can be used to connect to genuine AP and explore the Lateral movement to escalate to Domain Admin group.













nice idea about wifi hacking....thanks for sharing...iphone Support
ReplyDeleteFor those who didn't find the mentioned wireless adapter can also opt for Alfa AWUS036NHA. Other cards that are compatible with hostapd-wpe are mentioned in the below link.
ReplyDeletehttps://goo.gl/KwbU2o
What security settings in Windows would prevent a user from manually overriding the certificate warning? Can this be enforced via group policies? Are there versions of Windows/configurations where an untrusted certificate is blindly accepted without even prompting the user for confirmation?
ReplyDeleteWe are looking for salicylic acid here, which is known to get rid of all that nasty buildup from your scalp and hair. You may use another cleanser with salicylic acid, but Clean & Clear is widely used for this method and is fairly cheap. As mentioned earlier, Old Style Toxin Rid Shampoo is the best option out there to eliminate drug contaminants from the hair. There are six main types of drug tests: 1. Urine 2. Oral/saliva 3. Visit: https://www.urineworld.com/
ReplyDeleteBuy Lions WireThe Lions raced casino.edu.kg out to a halftime lead thanks to 5 straight scoring drives to open the game. Alas, NFL video games final two halves, and the second half was some of the the} worst football the Lions have performed all season–and that’s saying one thing in a yr the place Dan Campbell’s squad is now 1-6. "When adverts first appeared within the App Store in early iOS betas, many inside have been very upset," he wrote. "It was an insult to our clients. We pushed back strongly. After a gathering where management pretended to take heed to our issues, it was evident they'd no intention of adjusting their thoughts." Many eyes will therefore be on the launch — and also on its aftermath.
ReplyDelete