Mapping Network using Sharphound
Bloodhound is the de facto tool when it comes to mapping the network in the Internal Assessment's post exploitation phase. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory environment.
Earlier Bloodhound was using powershell (v2) script as ingestor to enumerate all the information. But this ps1 script was lacking threading capabilities, which plays important role in mapping large network's. So later that Sharphound a C# based ingestor was introduced which overcomes all and maps network seamlessly.
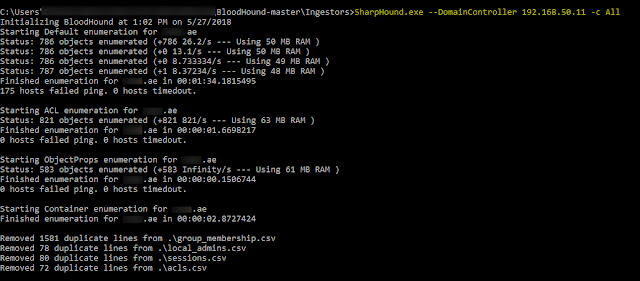
Lets see how to use this tool, suppose you compromised the valid internal Domain user credentials and you want to map the network to find path to privileged users. Download latest binary of Sharphound and from attacker machine you can connect to domain by typing runas.exe /netonly /user:<DOMAIN>\Username cmd.exe. If the credentials are correct, new cmd prompt would be launched with compromised user privileges. In newly opened cmd prompt, type below shown command were IP address represents DC IP and -c represents All (Group, LocalGroup, Session, LoggedOn, ComputerOnly, Trusts, ACL, ObjectProps, Container) collection methods.
Sharphound also have some new collection methods, to generate less requests over wire.
Stealth - Performs stealth collection methods. All stealth options are single threaded.
ExcludeDc - Excludes domain controllers from session enumeration (avoids Microsoft ATA flags :) )
Running above command would generate the multiple CSV's with all data. But if you want to enumerate more sessions in the network, Sharphound got new collection method called SessionLoop. It runs the session's collection loop for infinite time (or until you dont stop it), you would see the increase in size of sessions.csv file. This method enumerates more no. of sessions over the network in turn more path's to derivative admins.
Now you can take all the generated CSV and import in Bloodhound UI to draw different mapping and gain derivative admins. If you never installed Bloodhound, you can install using standalone powershell script by @SadProcessor on Windows 10 (64 bit machine).
https://blog.cptjesus.com/posts/newbloodhoundingestor



Great blog. All posts have something to learn. Your work is very good and i appreciate you and hopping for some more informative posts. Offshore dedicated hosting
ReplyDeleteHelpfull post ........
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteasdsdas
ReplyDeleteTo find computers connected to your PC through a network, click the Navigation Pane's Network category. Clicking Network lists every PC that's connected to your own PC in a traditional network. Clicking Homegroup in the Navigation Pane lists Windows PCs in your Homegroup, a simpler way to share files. windows 10 hosting
ReplyDeleteAmazing post..Keep updating your blog
ReplyDeleteDigital Marketing Course in Chennai
Digital Marketing Training in Bangalore
Good Informative Blog!!! Keep Sharing
ReplyDeleteSelenium Training in Bangalore
Selenium Course in Bangalore
Best Selenium Training in Bangalore
Selenium Training in Chennai
Best selenium training in chennai
Best selenium Training Institute in Chennai
The processor is among the foremost critical parts of the portable workstation since it allows the computer to operate. It can peruse the code put away within the memory of the computer and tell the other parts to do what the code states. flash storage
ReplyDelete
ReplyDeleteWonderful post and more informative!keep sharing Like this!
salesforce institute in bangalore
Salesforce institute in bangalore
It is really a helpful blog to find some different source to add my knowledge. IT Support Brisbane
ReplyDeleteĐặt vé máy bay tại Aivivu, tham khảo
ReplyDeletevé máy bay đi Mỹ
giá vé máy bay từ mỹ về việt nam
chuyến bay từ frankfurt đến hà nội
khi nào có chuyến bay từ nga về việt nam
giá vé máy bay từ anh về việt nam
chuyến bay từ Paris về Hà Nội
vé máy bay đi hàn quốc tháng 10
Hello, I must say it was a very helpful blog post. Very Informative and interesting as well, I am looking forward to reading more. Thanks for sharing.
ReplyDeleteIf you’ve been entrusted with a IELTS Coaching In Delhi and are looking for information, come here. They’ll consult with you and help you figure out what you need to know.